Intro
I love Supermicro, they make great boards and some of my favorite chassis. Typically I like to build my own servers so I’m not stuck buying hard drives just to get trays or subject to back doors out of the box. I build most servers from parts so I can pick the hardware I like and make sure I’m using what I consider to be the newest stable set. However, I recently stumbled across the fact that on older versions of Supermicro IPMI firmware the system will just give you the admin password.
The problem
IPMI is a standard remote management tool typically built into server class motherboards. This means you can remotely:
- Power cycle the unit
- Change some setup/BIOS options
- Monitor sensors (temp, fan levels etc)
- Open a console as if you plugged into VGA
- Access the machine, even if it is off
However, besides HTTP, other ports are open. It appears that Supermicro IPMI port 49152 will just hand over all your user credentials if asked correctly.
My board and setup
| Motherboard | X9DRi-LN4F+ |
| Current IPMI | ver 02.34 |
| Upgrade to IPMI | ver 3.29 |
My test on version 2.34
root@host:/# nc ipmi_host 49152 GET /PSBlock ▒ /▒ ▒adminADMINADMINTTadminpassword_here_for_free▒▒▒}▒▒▒oDDD@h▒L root@host:/#
It looks like there is a file “PSBlock” that contains most user info in plain text and the system will give it freely if you ask. Luckily Supermicro has already released a patch to address this issue.
You can apply the new firmware through the web interface:
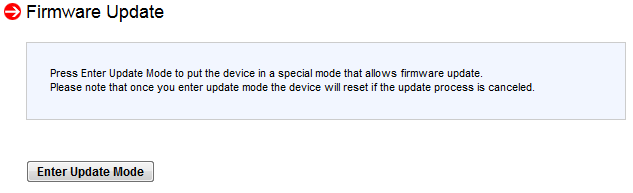
Once the firmware was applied port 49152 no longer replies so I’m not sure if they’re hashing the passwords now or if they just closed the port.
NMap before patch
Not shown: 95 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh Dropbear sshd 2012.55 (protocol 2.0) 80/tcp open http lighttpd 443/tcp open ssl/https? 5900/tcp open vnc VNC (protocol 3.8) 49152/tcp open upnp Portable SDK for UPnP devices 1.6.18 (Linux 2.6.17.WB_WPCM450.1.3; UPnP 1.0)
NMap after patch
PORT STATE SERVICE VERSION 22/tcp open ssh Dropbear sshd 2013.60 (protocol 2.0) 80/tcp open http lighttpd 443/tcp open ssl/https? 5900/tcp open vnc VNC (protocol 3.8)
However, once you perform the IPMI upgrade all of your settings and users will be lost. I don’t use the default ADMIN/ADMIN — and I strongly recommend disabling it — so I had to recreate my users for IPMI after the upgrade.
Password issue with IPMI firmware 3.29
I like to use complex passwords that include symbols, numbers and potentially spaces. However, when I recreated my user I found I couldn’t log in no matter how carefully I typed my password. I started to experiment and it became obvious that the HTML interface was truncating my passwords and not informing me.
I decided it would be worth figuring out exactly where the password breaks.
Why the new IPMI firmware breaks long passwords
Through trial and error I was able to determine when passwords start getting truncated
babiesbabies -- works babiesbabiesbabies -- works babiesbabiesbabiesbabies -- breaks
Now we know truncation occurs between 19 and 24 characters. A quick inspection of the HTML on the change password page shows
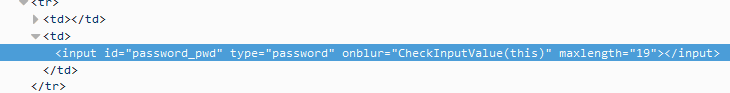
So there we go, it’s set to a max length of 19 characters in the submit. After finding this out “babiesbabiesbabiesb” works when the password was set to “babiesbabiesbabiesbabies”
How to get around the truncation and still set long passwords
After doing some digging I found that Supermicro has a Java based config utility called IPMIView.
Download this tool and launch it by calling IPMIView20.bat. You might need to add a line to the batch file that looks like:
set path=C:\Program Files (x86)\Java\jre7\bin
Chances are you if you don’t do this it won’t find your java binary.
What the tool looks like once it works
Using the above utility you can once again set longer — 19+ — passwords.
Conclusion
Definitely upgrade to the new version of Supermicro firmware because even if it’s just your LAN port 49152 is dangerous! However, if you like passwords that are longer than 19 characters you’ll need to use their IPMIView tool to set it.
Thanks
- Dan Farmer for publishing the original PDF — local mirror —
- Arstechnica for posting this issue http://arstechnica.com/security/2014/06/at-least-32000-servers-broadcast-admin-passwords-in-the-clear-advisory-warns/
- Zachary Wikholm for posting his findings on this originally http://blog.cari.net/carisirt-yet-another-bmc-vulnerability-and-some-added-extras/
- Supermicro for making great hardware and patching this problem quickly http://www.supermicro.com/index.cfm
Hi, thanks for this.
I was preparing to reset the IPMI password via a dos applet booted from USB. This just saved me the trouble.
I tried setting a 32ch password, and figured it was too long and got cut off. I just had to determine what the character limit was…your article helped me realize the length. I’ve logged in successfully and updated my records.
Thanks!